Data talks application
Security Within Data Talks
The primary causes of data breaches were insufficient multi-factor authentication and weaknesses in third-party services, alongside significant contributions from phishing and malware attacks.
To address these issues, we dedicate substantial time to training our employees on IT security risks and strategies to mitigate them, including enforcing multi-factor authentication across all our services.
All of our endpoint devices have disk encryption, malware/virus protection, and the operating systems are regularly updated with the latest security patches.
Infrastructure Security
Data Talks is built on AWS, one of the world's leading cloud providers.
AWS provides a robust, compliant infrastructure, certified with GDPR, SOC 2/3, ISO 9001, ISO/IEC 27001, and more. This ensures a secure foundation for our product and reinforces our commitment to high security standards.
Zero Trust Network
With the increased amount of data breaches that happen each year, it's no longer enough to define your network as an "Inside" trusted network and an "Outside" untrusted network.
Data Talks relies on the Zero Trust networking principles which treat no network as a trusted network.
Authentication and Permissions
We enforce Multi-Factor Authentication across all internal services, ensuring that even if passwords are compromised, unauthorised access is prevented.
Additionally, we implement robust Role-Based Access Control (RBAC) policies, granting only the minimum necessary access to services, applications, and employees. This approach effectively reduces the attack surface area and enhances security.
Data Security
All data traversing our networks is encrypted with TLS v1.2 or higher, ensuring secure transmission.
Customer data is logically separated and protected through unique accounts and authentication credentials, preventing any cross-contamination between customers.
Additionally, we use a key management service to encrypt all data at rest, ensuring a high level of protection for stored data.
Protecting our clients’ data
Interested in our policy and procedures? Read the following article written by Rumesh Athukorala, DevOps Engineer at Data Talks.
Data talks application
Strong security culture
We are committed to ensuring the security and protection of the personal information that we process on our clients behalf, providing a compliant and consistent approach to data protection.
Security development practices
Policy & Procedures
We are supporting our customers through preparation to enable the security of data, we have routines and policies that we ourselves follow strictly. In addition to that, during customer onboarding, we help out with ready-to-use templates for information audits.
The following are highlights of our preparation.
- Data Retention & Erasure our retention policy and schedule ensure that we meet the ‘data minimization’ and ‘storage limitation’ principles.
- Breach response procedures ensure that we have safeguards and measures in place to identify, assess, investigate and report any personal data breach.
- Information Audits:
- Customer-specific audits with well-defined templates for Legal Basis and Impact Assessment.
- Internal Audits with help of our Data Catalog to have control over what data we have.
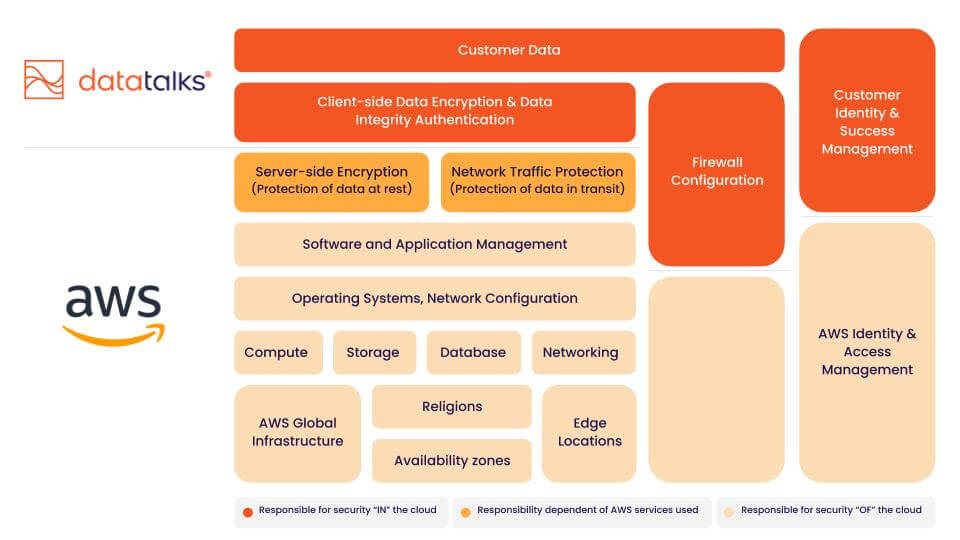
Shared Security Model with AWS
Data Talks CDP is built on top of the AWS cloud. That means the responsibility for the security of Data Talks CDP is shared between Data Talks and AWS.
We are responsible for the protection of the security IN the cloud while AWS is responsible for the security OF the cloud. AWS is therefore responsible for the underlying infrastructure such as the data center itself and the servers inside while Data Talks is responsible for the data stored on those servers.
Right of Access by the Data Subject
Article 15 in GDPR requires Controllers to give Data Subjects access to information, erasure, portability, restriction in processing and purpose for processing. At Data Talks we have implemented routines and technology to speed up the process for our customers (the Controller).
Data Privacy by Design
Data Talks CDP provides key features and functionality that will support your Data Security compliance now and in the future. Highlights are:
- Well defined and high level of automation for Data Onboarding
- Smart data model with a Business Key Vault
- ML-based and proactive security risk services
- Data Protection methods including functionality for depersonalization
We care about your security
Endpoint Security
Our endpoints are safeguarded according to our security policy, which includes securing the underlying infrastructure and ensuring all operating systems are consistently patched. Regular checks are conducted to verify that endpoint security meets our stringent standards, maintaining a high level of protection.
Vulnerability Management
In addition to identifying bugs and vulnerabilities through daily development activities, we have a dedicated process for proactively scanning the system for potential vulnerabilities. Any issues discovered are categorised and prioritised, enabling the development team to address them efficiently based on their severity and impact.
Quality Assurance
Every new feature developed by our team undergoes a rigorous testing protocol by our QA team, incorporating shift-left security testing to identify and address potential vulnerabilities early in the development process. This approach ensures our features are thoroughly vetted for quality, security, and reliability from the outset.
Incident Management
We have a well-defined incident management process for handling any security events that may impact the integrity, availability, or confidentiality of our customers' data. In the event of an incident, the security team assigns it an appropriate priority level and escalates it to the relevant team to ensure a swift and effective response.
Data talks application
Our Data Protection
Officer
“We are dedicated to safeguarding the personal information under our remit and in developing a data protection regime that is effective, fit for purpose and demonstrates an understanding of, and appreciation for the GDPR regulation.
We have a consistent level of data protection and security across our organization, however it is our aim to be fully compliant with the GDPR, PDPA and other national data protection laws.”

Rumesh Athukorala
DevOps Engineer at Data Talks
In a nutshell
The protection of our clients’ data and resources is our priority and therefore, we will continue to improve our security measures and keep up to date with the newest cybersecurity advancements. Finally, we will keep up with the newest regulatory laws so that we stay compliant.
Data Talks CDP – how it works

